- Juniper Encrypted Password Decrypt
- Juniper Encrypted Password Crack 1.1
- How To Crack Encrypted Password
KB ID 0000940
Problem
Decrypt Type 7 Cisco Passwords
The Internet is full of sites that have something like the tool below, tap your ‘encrypted’ password in and it will reveal the Cisco password.
As you can see I’ve specifically written ‘obfuscated’ above, because the password isn’t actually encrypted at all. All that happens is the Vigenere algorithm is used to obfuscate the password. While tools like the one above are all well and good, your Cisco router will do exactly the same for you, to demonstrate, paste the following into the tool above.
Hi Egarro, These are my thoughts: 1) MD5 Hashing is one way i.e we feed password into MD5 Hashing engine, output comes out as bunch of random characters.
- This example encrypts password t1meout1 and creates a password for privilege level 10. Enable and configure the password. The 0 keyword specifies that you are entering an unencrypted password.
- To recover the password and configuration: Connect a console cable to the Master EX Switch in the Virtual Chassis. Power Off all members other than the Master. Reboot the Master from the console or from the LCD panel.
107D1C09560521580F16693F14082026351C1512
Hopefully you will get the password Sup3rS3cr#tP@ssword.
Your router can also convert that to clear text for you;
Juniper Encrypted Password Decrypt
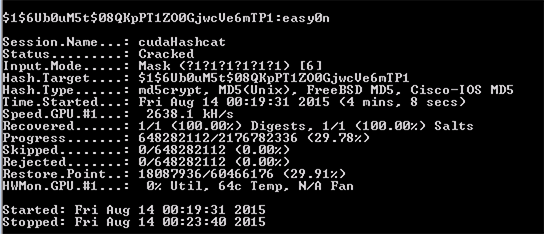
So whats the point of these type 7 passwords? Well the only real benefit of them is if someone is looking over your shoulder while you are looking at the config, they can’t see actual passwords in the config.
The passwords in my config are in clear text? That’s because there are three levels of password storage 0 (not encrypted), 7 (weakly encrypted), and (5 strongly encrypted). If you want to convert your config to display them as 7 you need to enter the service password-encryption command;
If Type 7 passwords are so weak, how do I use Type 5 passwords? When creating accounts use the secret command like so;
Displays in the config as;
username petelong secret 5 $1$VkQd$Vma3sR7B1LL.v5lgy1NYc/
Decrypting Type 5 Cisco Passwords
Decrypting a Type 5 Cisco password is an entirely different ball game, they are considered ‘secure’ because they are ‘salted’ (have some random text added to the password to create an MD5 hash) however that random salt is shown in the config.
Well armed with the salt and the hash, we can use exactly the same method that Cisco use to create the encrypted password, by brute force attacking the password, this might sound like a difficult piece of hacking ninja skill, but we simply use openssl on a Linux box (here I’m using CentOS 6.5), all you need is a wordlist.txt file (search the Internet).

Feed openssl the salt, and a piece of the hash (see the example above), and it will run through, (grep) the wordlist until it finds a match, where it spits out the decrypted password an the original hash like so;
The decrypted password is SECRETPASSWORD
Note: The limitation here is the password has to be in the wordlist.txt file,but if you are adept at searching the Internet there are some impressive wordlist files out there, just make sure you use one that has full line breaks. Also remember, the longer the wordlist, the longer it takes.

Related Articles, References, Credits, or External Links

NA
Have you ever wondered how Junos stores your passwords in configuration? And is there a difference between this one:
Juniper Encrypted Password Crack 1.1
and this one:

How To Crack Encrypted Password
Actually, the difference is significant: $1 passwords are “salted” SHA-1 hashes (“salted” means – the calculated hash is different every time, even if the password is the same), and the $9 passwords are just scrambled ones and can be easily reverted to the original plain-text form.
There is an online tool for that, or if you prefer a locally working script, there are some on the Internet, such as this one (Python 2 and 3):
In conclusion, although user’s passwords ($1 ones) can’t be easily recovered from a leaked config, your protocol authentication, FTP password, RADIUS secret, IKE pre-shared key, and some other sensitive keys can be derived from it. So make sure to keep your config backups in a secure place. Bmw manager mac os format.
